Organizations Announced
Until 12th of February, I haven't heard of OWASP. All I knew
was, okay; I am doing GSoC this year. I was going through the
list of accepted mentoring organizations for GSoC-2018 one by
one. At that point, I intend to pick an exciting Java project.
That's all, no unique preferences. Some organizations my eye. I
spent more time looking at their ideas. I made a note of such
organizations, ideas and kept traversing through the list. When
I hit OWASP, my traversal entered a
break
statement. In fact, my quest to find a suitable GSoC project
ended. A new pursuit to become a Computer Security Professional
began.
After finalizing the organization, I ,
- went through the guidelines
- read the “ Hacking Zap” blog posts
- looked at my first IdealFirstBug(#2332)
- looked at second IdealFirstBug(#173)
- took the Pluralsight course Getting Started with OWASP Zed Attack Proxy (ZAP) for Web Application Penetration Testing
- played with OWASP-BWA
- took the Pluralsight course Ethical Hacking: Hacking Web Applications
- played with OWASP-BWA and ZAP for some time
Submitted Proposal
The more I learn, the more I found to learn. I took quite a
long time to construct an implementation plan for the
IdealFirstBug
. That was discouraging and questioned me if I am the suitable
person to apply.
I was confident enough that
- I satisfy the project requirement
- I have a strong desire to do the project
- I have put a good effort on it
This confidence pushed me to go forward, and I submitted the proposal.
After submitting the proposal, I started familiarizing with the development environment and related technologies.
- took the Pluralsight course Eclipse Guided Tour for Java
- took the Pluralsight course Eclipse for Java Developers
- opened my first pull request (#1534)
- took the Pluralsight course Mastering Java Swing-Part 1
- took the Pluralsight course Mastering Java Swing-Part 2
- took the Pluralsight course Mastering Java Swing-Part 3
- Swing concepts practice code
Community Bonding
Hooray! I got selected
Let me first thank my mentors for their great support. Within
this bonding period the student is expected to familiarize with
the community practices and processes, work on project related
issues and work with the mentors and other organization members
on refining the project plan and of course go through the
documentation.
I had a kick off meeting on
26th April with my mentors. The meeting spanned for 45 minutes.
We discussed the goals of this community bonding period, the
importance of this project and what the community is expecting
from the successful completion of the project in general.
Following is the summary of the works done during the community
bonding period.
- Went through contributing.md, development rules and guidelines, add-on development wiki pages
- Start a blog for GSoC project
- Introduce in the ZAP Dev Group
- Setting up the development environment
- Start building up a list of different authentication mechanisms
- Start building up a list of examples
- Add support for dynamic fields in Form-based authentication method #2182
- Work on detailed plan for the project
Coding Phase-1
- PR: add support for dynamic fields in Form-based authentication method (#4682)
- Spring security requirement study
- create testing applications
- go through authentication related issues, posts in ZAP user, developer group
- PR: refresh cookie before each login request (#4696)
- PR: help contents for automatic acsrf token submission support in form-based authentication (#193)
- document setting up vulnerable apps for authentication
- go through existing code (as suggested in this comment) to get started with authentication status scanning setting up vulnerable apps for authentication
- brainstorm UI for AuthenticationHelperDialog
- complete first evaluation
Coding Phase-2
- Work on detailed plan for the project
- create ExtensionAuthenticationHelper
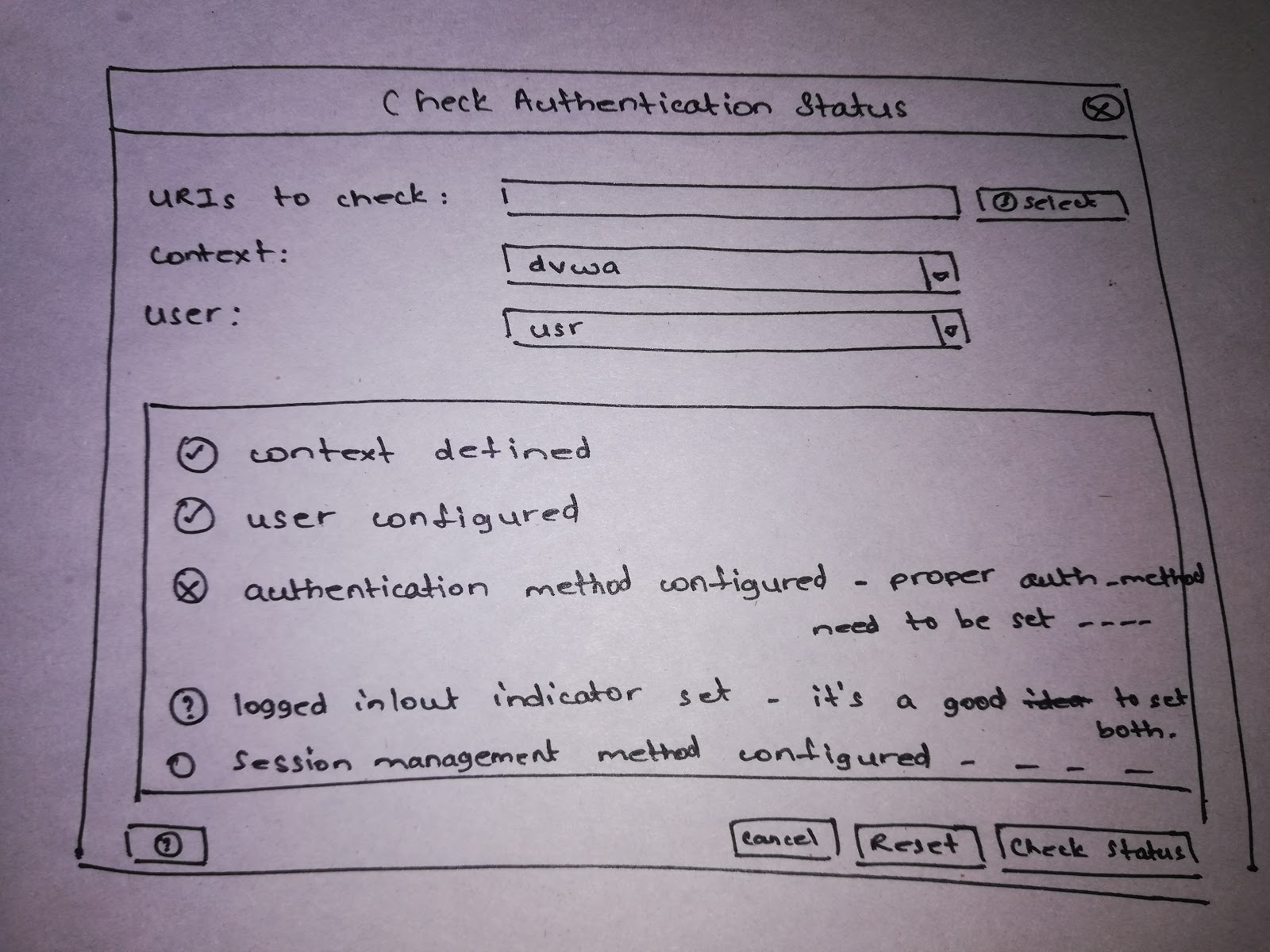
- create AuthenticaitonHelperDialog UI from which the pen tester can select Target, Context, User and start authentication status scanning.
- crete AuthenticationConfigurationChecklistPanel to indicate status of required configurations
- create PopupMenuItemCheckAuthentication that allows the pen tester to initiate the AuthenticationHelperDialog by right clicking a SiteNode and selecting Check authentication option.
- create AuthenticationStatusTableModel, AuthenticationStatusTable and AuthenticationStatusTableEntry classes to show necessary data to the pen tester
- create AuthenticationStatusPanel UI in which the authentication status scan result will be updated and the pen tester can start, stop, pause, resume, and analyze the HttpMessage
- requirement study: concurrency in Java
- create AuthenticationStatusScanController to control multiple authentication status scans
- create AuthenticationStatusScanner that matches each HttpMessage's Header, Body with provided logged in indicator or(and) logged out indicator and determine authentication status from it
- complete second evaluation
Coding Phase-3
- add links to relevant Session properties dialog for each checklist item in AuthenticationConfigurationChecklistPanel
- remove redundant ToolTips in AuthenticationConfigurationChecklistPanel
- add refresh button in AuthenticationConfigurationChecklistPanel to rerun the checks with updated settings
- internationalized the Strings that are shown in UI
- add a hint panel with settings button in AuthenticationConfigurationChecklistPanel that tells the next best step and leads to the relevant properties dialog when the button is clicked
- fix alignment problem in AuthenticationHelperDialog using reflection
- add AuthenticationHelperOptionsPanel that allows the pen tester to add regexes which are excluded from authentication status scanning
- automatic configuration for HTTP basic scheme
- PR: necessary core changes for the add-on (#4898)
- auto configuration logic for HTTP digest, NTLM
- bug fix: in determining authentication status
- write test cases for determining authentication statusli>
- auto configuration logic for post based authentication schemes
- auto configuration when spidering
